If you think your site may have been hacked, there are some signs you can look for to confirm your suspicions
One of the most frustrating experiences you could ever encounter as a WordPress user is finding out that your site has been hacked. One minute your website is really humming along and bringing in traffic, and maybe even revenue. And then next thing you know, you discover something’s very wrong with your WordPress installation.
Websites are becoming increasingly important to all businesses. They help handle everything from customer data management systems, e-commerce transactions and on the whole lot of other responsibilities that usually slow down business due to the extra amount of work involved in each task.
WordPress hacks come in many forms, shapes and sizes. This means, as WordPress site owners, it’s important to know all about the common reasons why WordPress sites get hacked! In this guide we will discuss the common reasons WordPress sites get broken into along with simple steps you can take to secure your site.
To protect websites against hackers, there are a few safety precautions that all site owners should take to keep their site secure and safe from the bad guys.
This article is all about finding out if your WordPress website has been hacked or not and letting you know how to deal with it if your WordPress site turns out to be compromised by hackers.
- You notice sudden, unexplained spikes in traffic.
- Your site starts displaying strange or unwanted content.
- You can no longer log in to your site.
- Your site is running slow, or not at all.
- You receive strange messages or comments from unknown people.
- You find new, unknown users on your site.
- Your site’s design or layout has changed without your knowledge.
- You see strange code or files in your site’s directories.
- You receive security warnings from your hosting company.
- You suspect that your site has been blacklisted by search engines.
If you notice any of these signs, it’s likely that your WordPress site has been hacked. Take immediate action to secure your site and protect your data.
Are you worried that your WordPress website might be hacked? Here are the top 10 signs to look out for that indicate your site has been hacked. From strange new user accounts to sudden changes in website content, these are the telltale signs that you’ve been hacked.
Don’t wait until it’s too late – take action today to secure your site and protect your data.
10 signs Your WordPress Site is hacked badly
1. Sudden Drop In Website Traffic
If you log into your Google Analytics account and notice a dip in interest for your website, there may be a reason for concern. If this is happening over a period of time, then there could be something wrong with your site which leads to below-standard click-thru ratios. You can check this by using the Google Webmaster Tools or Google analytics.
You can use both tools to check for any incorrect urls that are displayed on your site or if your content has been duplicated by other websites – even though Google Analytics is set up properly, then this could be a sign that your WordPress site is hacked.
If you become aware that your blog is performing much more poorly than you have come to expect from it, your WordPress site could be hacked. There are a variety of indications that could be pointing this out.
For example, if visitors to your website are being redirected to other pages or sites, for instance by pop-up advertisements; or if Google has already begun to blacklist your site based on feedback it has received about the quality of its content. I
The easiest way to monitor the outbound traffic on WordPress sites is to use the best google analytics plugins for WordPress . Although one starts with setting up Google analytics correctly, through logging the key data points of each visit to the site (user engagement, bounce rate etc.)
We recommend that it is important to watch out for links that are being used across sites outside of your own network linked in some way with your organization or business
Each day, Google blacklists around 10,000 infected websites. To avoid your site landing on the ‘malicious software’ list, it’s important that you stay safe online and on WordPress with a robust security system, you can make use of this tool quickly see your safety report.
2. Site is blacklisted by Google or other search engines
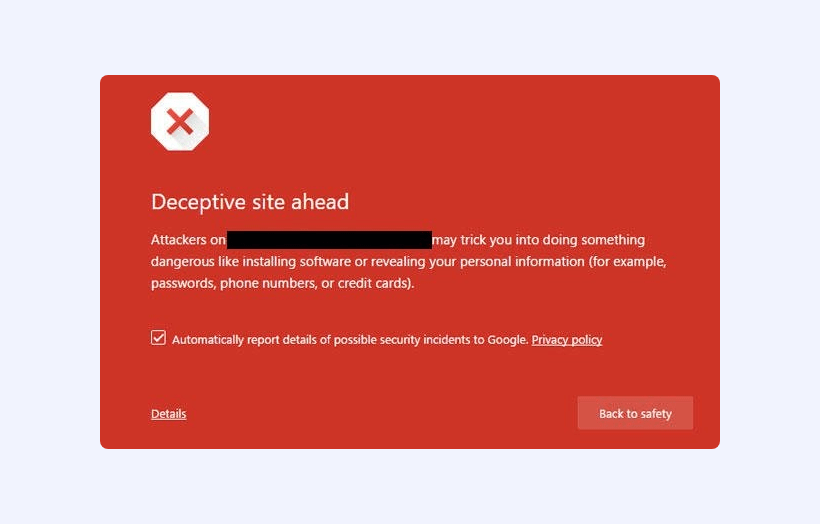
An increasing number of users who access your website through Google Chrome will be seeing a message from Google Chrome with a warning message saying that your website may be hacked. This message is shown when your website has been blacklisted by Google Safe Browsing as it has been identified as harmful to its users.
The sudden drop in traffic could be because either Google’s safe browsing tool is showing these warnings to users or you have received bad reviews on some of the sites you have advertised on.
Please check through Safe Browsing for more details about any potential threat on your site, see what could be doing this and update them accordingly to fix any issues.
3. Your site’s front-end or back-end suddenly looks different

Most hacking attempts occur on the front page, or home page of your website. You can test all pages of your website and make sure that they are secure by running a security script such as W3C HTML Validator. You can use it to find out if any part of a web page is inaccessible to search engines and update their access permissions.
These scripts help you quickly notice if there is any malicious activity going on with your website, which may suggest that your site has been hacked by a hacker!
Many times your homepage will be hacked and damaged for many reasons. The main reason is to get the attention of others through notoriety or a prank that goes viral, so there is no real intent to fundamentally destroy your website.
In this case make use of trusted wordpress backup plugin so if anything strikes to your website, you can easily have backup and get access to it in matter of second.
4. Spammy Links added to your website
Malicious code injection is one the most common types of malware infections typically found on WordPress sites. These infections create a backdoor that gives intruders access to change your core WordPress files and database.
Some of these hacks can be tricky to find. Links are sometimes added to the footer of your website, but are more often injected into your database like a hacker would do to sneak in unnoticed and add bad links somewhere in your source code. Finding them is not easy though since some of these backdoors were specifically designed to stay hidden.
They could be anywhere including inside plugins or themes that you are using so you need to check them carefully before deleting any link especially using a simple Google search.
Incase if you are using any of nulled plugins or themes in your live WordPress website that contains data of user then your website is 100% already hacked because of using such nulled themes and plugins from unknown developer.
Take a look at our sister site to learn more about case on why user must avoid nulled themes and plugins also the methods to find which wordpress theme a particular site is using.
5. Unusual activity on your WordPress site logins
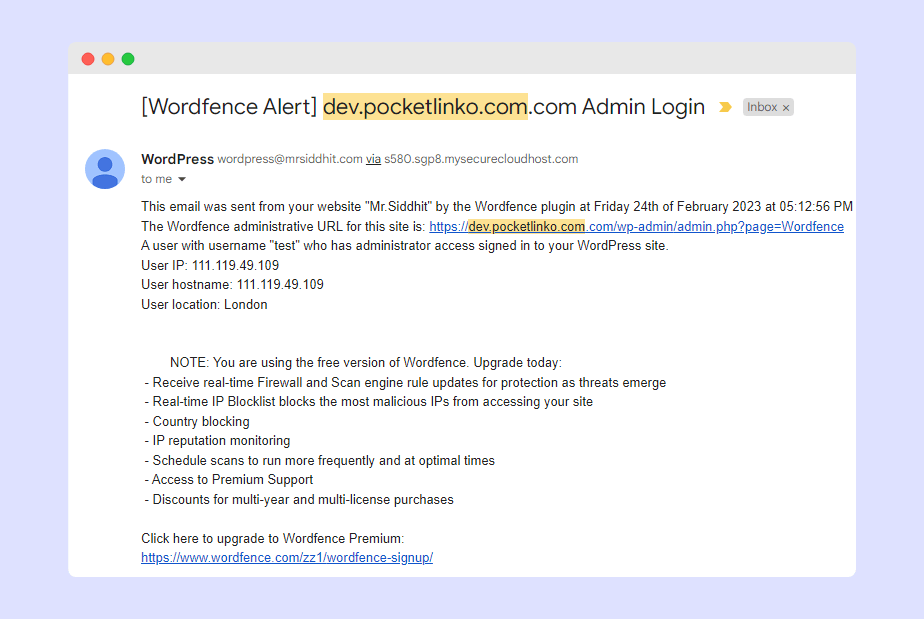
If you’re having trouble logging into your WordPress site, it’s unlikely that hackers have deleted your account; they would normally just leave the access in place.
In certain instances, if a computer has been infected by a virus or other malware there is a chance that these problems could result in the deletion of your WordPress account.
If your website welcomes user registration, and you aren’t implementing a spam registration protection, the only thing that is common here is the presence of spammers who will most probably try to register those accounts to publically post advertisements or send you junk mails.
To prevent such things, we suggest you start using a software like (Wordfence security plugin) if you don’t have one yet. You can set it up in just a few minutes, no coding knowledge required or take a look at our best security plugins for WordPress website.
However, if you do not remember when you allowed user registration and are still seeing new users showing up in WordPress, then your site may have been hacked.
6. Strange code or files in your site’s directories.
If files on your website have been changed, added or removed, it could be a sign that your site is getting hacked! It’s essential to have a notification system in place that will alert you when something happens when it comes down to compromising what’s on your site.
You can investigate by comparing the changed file to a version in a recent backup and if you feel like someone malicious was involved (or might have been) there are some experts out there who can help you.
Using a WordPress security plugin like Wordfence security can help you track changes in your file system. Since it can generate the number of notifications, you can exclude files and directories in File Change Detection settings.
It is okay to exclude directories that you know are going to be regularly updating. For example: backup and cache files and there will be fewer notifications.
7. Your site is running slow, or not at all

When a hacker wants to infect your site with malware or steals your password, they’re attacking it. Since most website infections come from installed must have WordPress plugins not updated in a while by the owner, this is typically referred to as a Zero-day plugin attack . Brute force attacks are similar but instead of zero days, hackers try randomly until they find something successful.
As the creator of your own website, it is possible that your site may become the target of a DoS or DDoS attack. These attacks can be launched by hackers using several computers and servers from all over the world to send malicious requests which overload your system with too many requests for a website to be able to handle.
The result could still be what you want – increased traffic and visibility – but if the methods used are illegal then those perpetrators will actually experience legal repercussions including imprisonment.
9. Malicious Popups or Pop under ads on your website
It’s not uncommon for a website to see a drop in performance. If you see popups that redirect visitors to unwanted websites, chances are it could be an attack site. The threat is mostly directed towards Google AdSense advertisers due to the fact that it targets peoples’ clicks in order to profit on pay-per-click ads.
These hidden systems are programmed to hack a website’s page ranking in Google search results. Content they provide is usually spam, usually appearing in the form of comments underneath blog posts. There are no pop-ups and it purely appears if you have a popup blocker disabled.
10. Unexpected Core WordPress Files are changed

If your core WordPress files have been changed or modified in any way, it’s important to know that this may be an indication that your WordPress site is hacked.
Hackers commonly modify core WordPress files and place their own code inside of them. They may also create files with names similar to those of the core WordPress files.
If you notice a file in your WordPress directory that has a different file size compared to others files, or you see an unfamiliar file name, there is a possibility that it’s an infected file. Having an active IT support partner or your WordPress hosting team can also protect against these types of threats.
If your core WordPress files are changed or modified in some way, then that’s an important sign that your WordPress site is hacked. If you are having trouble with your website hosting and want to migrate to another you take a look at our guide on “Choosing the best WordPress hosting provider“
The easiest way to track those files is by installing a WordPress security plugin on your online business website. You can also manually check your WordPress folders to look for any suspicious files or scripts.
11. Randomly Redirect to spam websites
If you suspect that your website has been hacked, you could try typing the address of the page that is giving you trouble into the address bar of a different browser or device.
You can also contact your web host, and if they appear to not have done anything to patch up the security hole that may have allowed the hack, result in their support team getting back to you quickly with insight on how to fix things up (not to mention knowing how to keep them from being hacked again).
What is WordPress Vulnerability?

A WordPress vulnerability is a flaw in the software that can be exploited by attackers to gain access to WordPress sites or systems. WordPress is a popular content management system (CMS) used by millions of websites and businesses.
While WordPress is generally a secure platform, vulnerabilities can be introduced when third-party plugins or themes are used. Attackers can exploit these vulnerabilities to inject malicious code or take over a WordPress site.
WordPress vulnerabilities are often discovered and patched by the WordPress community. However, if a vulnerability is not patched, it can be exploited by attackers.
It is important to keep your WordPress site and plugins up-to-date to reduce the risk of vulnerabilities. You can also use a security plugin to help scan for and protect against vulnerabilities.
4 Common Methods Used to Hack into WordPress Websites
There are a few common methods used to hack into WordPress websites. One of the most common is brute force attacks, where hackers use automated tools to guess the username and password combinations until they find one that works.
Another common method is SQL injection, where hackers insert malicious code into SQL database queries in order to gain access to sensitive data.
Hackers also often exploit vulnerabilities in WordPress plugins and themes. Oftentimes, these vulnerabilities are not discovered until after a plugin or theme has been released, which is why it’s important to keep your WordPress site up to date.
Outdated plugins and themes are one of the most common ways that hackers gain access to WordPress websites.
Below are the most common methods hacker implement to hack into any WordPress website:
A). BruteForce: This form of attack, known as a brute force attack, is one of the most common ways for hackers to gain access to a website.
It exploits the simplest method of gaining access to a site: by trying to guess usernames and passwords, over and over again, until they eventually get it right. In many cases, hackers will use automated tools to carry out these attacks, which makes them even more dangerous.
WordPress sites are particularly vulnerable to brute force attacks by default because the system allows unlimited login attempts. This means that if a hacker is determined enough, they can keep trying different combinations of usernames and passwords until they finally find one that works.
Once they’ve gained access to your site, they can then do all sorts of damage, from stealing sensitive information to injecting malicious code or even taking your site offline entirely.
To protect your site from brute force attacks, it’s important to use strong, unique passwords and to limit the number of login attempts allowed. You can also use security plugins or services that are specifically designed to detect and block these types of attacks.
By taking these steps, you can help ensure that your site remains secure and protected against even the most determined hackers.
B). Cross-site scripting (XSS): This is a type of security vulnerability that allows an attacker to inject malicious code into a web page viewed by other users. This technique is one of the most common hacking methods used today.
WordPress, like many other web applications, is susceptible to XSS attacks. Even though WordPress has implemented measures to prevent XSS attacks, many new WordPress plugins are still vulnerable.
Furthermore, some old plugins are also vulnerable because they were created before XSS prevention was added to WordPress. It is crucial to stay vigilant against XSS attacks to ensure the security of your website and its users.
Hackers can use XSS attacks to steal sensitive information or spread malware to unsuspecting users. An attacker can inject malicious code into a web page by exploiting vulnerabilities in a WordPress plugin or theme.
Once the malicious code is injected, it can execute on the user’s browser and perform actions such as stealing login credentials, redirecting the user to a phishing website, or even taking control of the user’s computer.
The best way to protect against XSS attacks is to keep your WordPress site up-to-date and use security plugins that can detect and block these types of attacks. When selecting WordPress plugins,
It is important to research the plugin and its developers to ensure they follow secure coding practices. Additionally, it is recommended to limit the number of plugins used on your site and to regularly audit your site for any vulnerabilities.
In summary, cross-site scripting is a common hacking method used by attackers to inject malicious code into web pages viewed by other users.
WordPress is susceptible to XSS attacks, and it is crucial to stay vigilant against them by keeping your site up-to-date, using secure plugins, and regularly auditing your site for vulnerabilities. By taking these precautions, you can help ensure the security of your website and protect your users from harm.
C). Web Server Code Execution: Code injection attacks occur when a malicious hacker or coder attempts to force their code into an existing program, effectively overriding its original programming.
This can be done through various means, such as inserting code into input fields or manipulating URL parameters. Once the hacker’s code is successfully injected, it can take complete control of a vulnerable web server, potentially causing significant damage or exposing sensitive data.
One common type of code injection attack is SQL injection, where attackers inject malicious SQL code into input fields, aiming to steal or manipulate sensitive data stored in a database. Another type of injection attack is cross-site scripting (XSS),
Which involves injecting malicious scripts into web pages viewed by other users, potentially allowing attackers to steal user data or take control of their accounts.
To prevent code injection attacks, it is essential to use secure coding practices and implement input validation and sanitization techniques. Additionally, regularly updating web server software and applying security patches can help to mitigate the risk of vulnerabilities being exploited by attackers.
D). SQL Injections: It is a type of web application attack where an attacker can execute his or her own SQL code on a server, without the website owner or the web application being aware that the end-data has been manipulated.
This type of attack can be carried out by exploiting vulnerabilities in web applications that do not properly validate user input. Once the attacker gains access, he or she can modify, delete, or extract sensitive data from the database. It is important for web developers to use secure coding practices and employ input validation techniques to prevent SQL injections.
Additionally, regular security audits and vulnerability assessments can help identify and mitigate potential SQL injection vulnerabilities in web applications.
Finally, some hackers will gain access to WordPress websites through server-side vulnerabilities. This can happen if a WordPress website is hosted on a server that has not been properly configured or that has outdated software. By gaining access to the server, hackers can then gain access to all of the websites that are hosted on that server.
All of these methods are common ways that hackers gain access to WordPress websites. By understanding these methods, you can help to protect your own WordPress site from being hacked.
Conclusion
WordPress is one of the most widely used headless CMS platforms currently in existence. While it offers powerful functionality and a range of potential applications, this also means that it can be particularly vulnerable to hackers for different reasons. In fact, WordPress outshinws the other 2 most popular content management systems when it comes to reported cases of cyber attacks: Joomla! and Drupal.
To give you an idea – on average there are more than 20Million security incidents per month because of WordPress sites being compromised and hacked via various backdoor Trojans.
In conclusion, WordPress is a popular content management system that is used by millions of websites and blogs around the world.
However, its popularity also makes it a target for hackers. If you suspect that your WordPress site has been hacked, there are a number of signs to look for, including sudden spikes in traffic, changes to the design or layout of your site, and the appearance of strange code or files in your site’s directories.
By being aware of these signs and taking steps to protect your site, such as keeping WordPress and plugins up-to-date and using a security plugin, you can help reduce the risk of your site being hacked. If you do notice any of these signs, it is important to take immediate action to secure your site and protect your data.
We hope that this article has helped you learn about some of the most common WordPress security threats and how you can protect your site from them. Although there is a lot of advice out there on how to secure WordPress websites, there’s no substitute for being aware of the ways your site can be attacked.
Once you know what signs to look out for, you’ll be able to take the right action to protect your site. If you have any questions on the topic, please feel free to comment down below.












